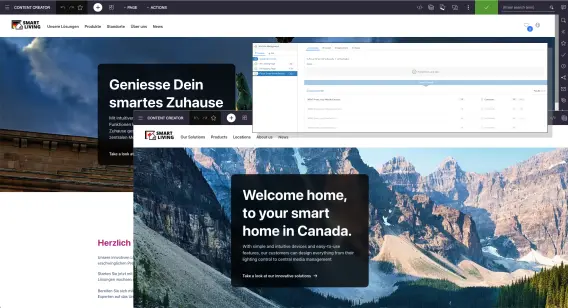
The FirstSpirit CMS is more than just a content management system. It's a strategic platform that enables your organization to operate with greater efficiency and intelligence and reach a wider spectrum of customers across all channels.
Experience the FirstSpirit Difference:
Intelligent, Flexible, and Scalable.
AI-Driven Content Innovation
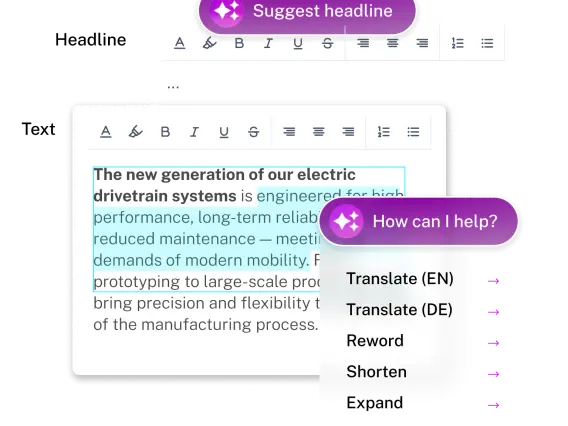
FirstSpirit's built-in AI Assistant Suite revolutionizes content creation and digital experience management to streamline workflows, create faster, work smarter, and deliver exceptional results.
Empowering User Experience
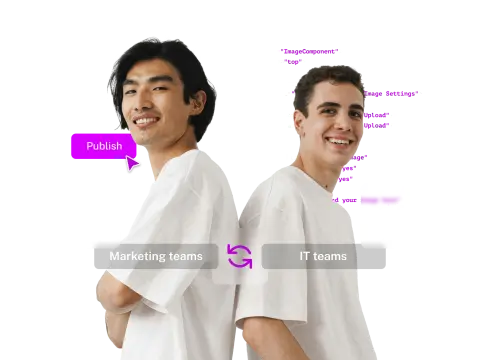
Equip your teams with intuitive tools that empower them to create, manage, and deliver engaging content efficiently with a combined WYSIWYG and Content Hub experience.
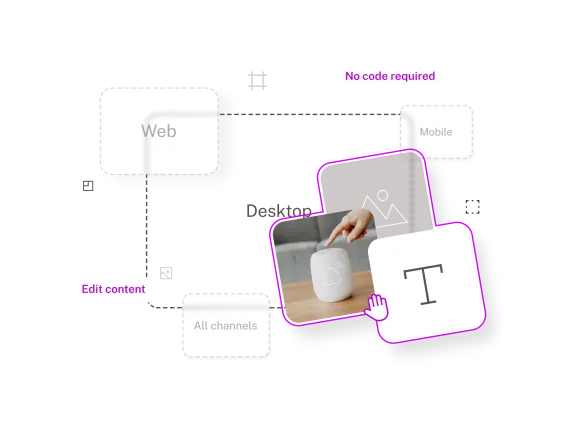
FirstSpirit CMS provides the adaptability needed to tailor content experiences for specific channels and audiences, fostering greater engagement and broader reach.
FirstSpirit CMS provides the adaptability needed to tailor content experiences for specific channels and audiences, fostering greater engagement and broader reach.
Designed for Integration
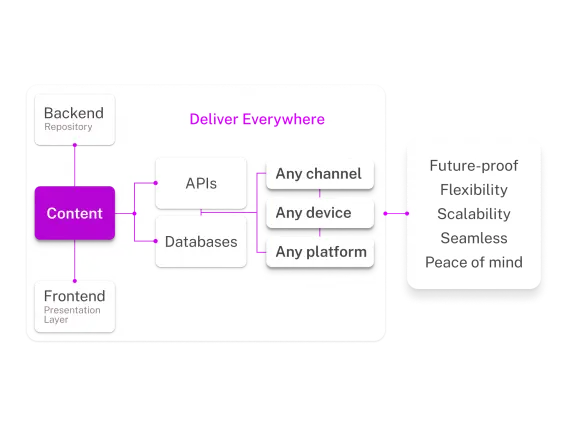
With universal flexibility, FirstSpirit offers a flexible framework for seamless third-party integrations into your existing MarTech stack.
Our decoupled architecture supports any language, framework, or deployment method – static, dynamic, headless, or hybrid – accelerating deployment and reducing costs in digital transformation.
Our decoupled architecture supports any language, framework, or deployment method – static, dynamic, headless, or hybrid – accelerating deployment and reducing costs in digital transformation.
Enterprise Scalability & Controls
Maintain complete oversight of your content ecosystem with robust governance features, version control, and workflow management. FirstSpirit CMS provides the structured environment necessary for large-scale, international content operations, ensuring trust and precision in every delivery.
FirstSpirit revolutionizes digital experiences with AI-driven content creation and seamless cross-channel deployment.
Its decoupled architecture ensures speed, flexibility and effortless integration, enabling businesses to scale, adapt, and drive revenue in an evolving digital landscape
The Foundation for Global Content Excellence
Experience the power of a CMS designed for the demands of complex international businesses – one that brings together control and flexibility in a structured and logical manner.
50%
Faster Time-to-Market
for Product and Brand Communications
for Product and Brand Communications
25x
Improvement
in Publication Efficiency
in Publication Efficiency
60%
Increase in Operational Efficiency
through Integrated AI
through Integrated AI
_homepageheader.webp)